Most companies don’t get hacked because attackers are brilliant; they get hacked because humans are predictable.
In 2026, cybercrime isn’t about lone hackers in hoodies. It’s about billion-dollar ransomware-as-a-service platforms, AI-generated phishing emails, deepfake CEOs tricking finance teams, and state-sponsored groups turning cyberspace into a permanent warzone.
Welcome to the digital battlefield.
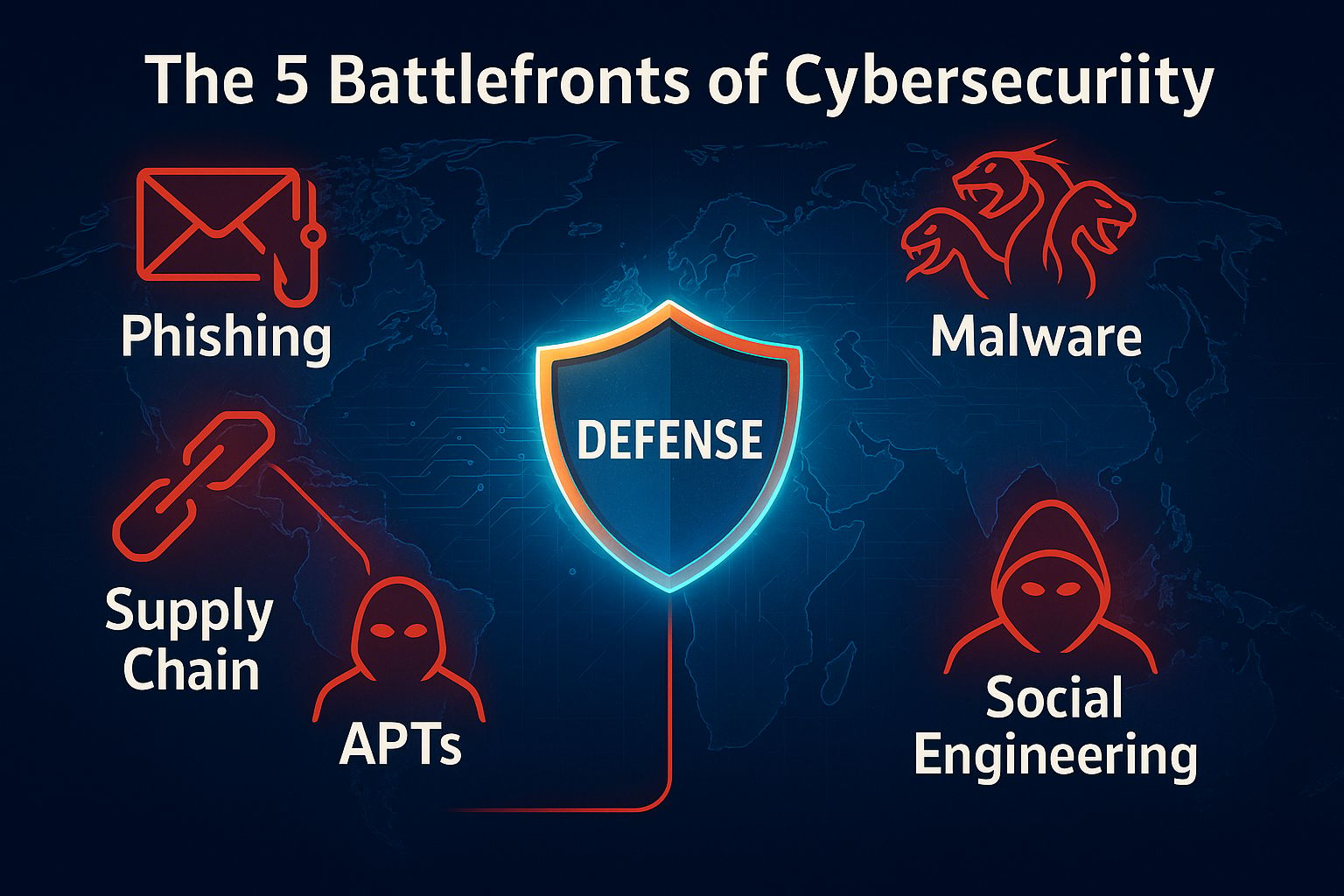
The 5 Battlefronts of Cybersecurity
To make sense of the chaos, I group today’s attacks into five battlefronts every leader should understand:
1. Phishing – The Shape-Shifter
It’s still the #1 attack vector because it exploits psychology, not firewalls.
Old-school spam → now AI writes flawless emails.
Fake invoices → now deepfake audio of your “CEO” asking Accounts Payable to wire €5M.
Smishing/vishing → SMS and calls pretending to be your bank, cloud provider, or even HR.
The scary part? You can’t firewall gullibility.
2. Malware – The Hydra
Malware mutates faster than defences.
Ransomware-as-a-service has created a franchise model of crime.
Polymorphic malware rewrites itself to evade detection.
State-sponsored malware targets critical infrastructure — from power grids to hospitals.
The result: it’s not “if” you’ll be hit, it’s “when.”
No zero-day needed when people overshare on LinkedIn.
Pretexting: “Hi, I’m IT. Can you reset your password?”
Baiting: “Free USB drives at the conference.”
Quid pro quo: “I’ll help you if you just…”
Your colleague Dave clicking a fake DocuSign link will always be scarier than some unknown malware in the wild.
4. APTs – Siege Warfare
Advanced Persistent Threats (APTs) are cyber slow-cookers.
Often state-backed.
Hide inside networks for months.
Use zero-day exploits invisible to antivirus.
Think of it as digital espionage — patient, strategic, devastating.
5. Supply Chain Attacks – Trust as a Weapon
Why hack you directly when attackers can compromise your vendor?
SolarWinds, NotPetya — we’ve seen it before.
In 2026, software supply chains are bigger, cloudier, and harder to secure.
If your weakest vendor gets hacked, so do you.
The New Layer: AI vs AI
Both sides are using AI:
Attackers → generate phishing emails, crack passwords, and test malware against AI-driven defences.
Defenders → anomaly detection, predictive alerts, automated incident response.
The uncomfortable truth? AI doesn’t eliminate the human factor — it amplifies it. Leaders still need judgment, context, and trust to make the right calls.
The Cyber Defence Playbook (8 Steps)
Cybersecurity isn’t about “perfect protection.” It’s about resilience. Here’s a practical defence plan:
Audit your assets → Know what you have before defending it.
Access control → Enforce MFA + least privilege.
Secure networks → Firewalls + segmentation.
Malware defence → Reputable AV + EDR (endpoint detection & response).
Educate your team → Simulate phishing, build muscle memory.
Backups → Regular, offsite, tested.
Incident response plan → Don’t improvise during a breach.
Stay informed → Threat intelligence + continuous adaptation.
Culture and Collaboration: The True Shield
Here’s the uncomfortable truth: most executives don’t like:
Cybersecurity isn’t an IT problem. It’s a leadership problem.
If your culture tolerates sloppy habits, you’re vulnerable.
If your vendors aren’t vetted, you’re vulnerable.
If your team is too scared to admit they clicked a bad link, you’re vulnerable.
Cybersecurity resilience comes from leadership, collaboration, and trust — not just firewalls.
Free Resource
📥 Download: The Cyber Defence Checklist (PDF)
Covers the 5 Battlefronts explained above.
8-step Defence Playbook to apply immediately.
Team training exercises to build resilience.
👉 Available free for all subscribers.
The digital battlefield isn’t going away. Every month brings new zero-days, ransomware groups, and scams. But the fundamentals remain the same:
Attackers exploit human behaviour.
Defenders win with awareness, discipline, and resilience.
Cybersecurity isn’t about stopping every attack. It’s about making sure your organisation is too resilient to break.
Because in the end, your greatest vulnerability is human, and so is your greatest defence.
👉 Upgrade to Cooking Agile Premium to get all premium content!